Which of the Following Is Not an Example of Pii
A list of passwords Correct The correct answer is. An organization cannot properly protect PII it does not know about.

Pii Protection How To Protect Personally Identifiable Information
List all potential future uses of PII in the System of Records Notice SORN D.
. Ensure employees are trained to properly use and protect electronic records. The following examples on their own do not constitute PII as more than one person could share these traits. Computer Science questions and answers.
WHICH OF THE FOLLOWING IS NOT AN EXAMPLE OF PII 1EDUCATION AND EMPLOYMENT HISTORY 2YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT VERIFY YOUR IDENTITY ORROOM NUMBER 3WEBSITES COOKIES PLACED ON YOUR LAPTOP 4. Name such as full name maiden name mothers maiden name or alias Personal identification number such as social security number SSN passport number drivers license number taxpayer identification number patient identification number financial account or credit card number and Department. Credentials for personal or business accounts b.
But they should still be treated as sensitive linkable info because they could identify an individual when combined with other data. However when linked or linkable to one of the above examples the following could be used to identify a specific person. Which of the following is NOT an example of personally identifiable information PII.
The means by which a persons true identity is intentionally exposed online. But they should still be treated as sensitive linkable info because they could identify an individual when combined with other data. Access to data and phone services d.
Non Personally Identifiable Information PII Data. Which of the following is NOT an example of personally identifiable information PII. Info such as business phone numbers and race religion gender workplace and job titles are typically not considered PII.
Partially or fully masked IP addresses. As a result this data does not require encryption before it is transmitted. Credentials for remote access software for business networks c.
Organizations should implement the following recommendations. Doxing is a method by which hackers obtain quasi-identifiers or personally identifiable information of. Info such as business phone numbers and race religion gender workplace and job titles are typically not considered PII.
No it is an example of an insulator and it is not an example of conductors. Non-PII data is simply data that is anonymous. This non-exhaustive list shows examples of what may be considered personally identifiable information.
What are some examples of non-PII. Aggregated statistics on the use of product service. Sensitive personal data - special category under the GDPR It is.
GOVT IDENTIFIER SUCH AS TAX ID. A list of passwords. The following list contains examples of information that may be considered PII.
WHICH OF THE FOLLOWING IS NOT AN EXAMPLE OF PII 1EDUCATION AND EMPLOYMENT HISTORY 2YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT VERIFY YOUR IDENTITY ORROOM NUMBER 3WEBSITES COOKIES PLACED ON YOUR LAPTOP 4. For example an office rolodex contains personally identifiable information name phone number etc. Reduce the volume and use of Social Security Numbers C.
Which of the following is not an example of PII. GOVT IDENTIFIER SUCH AS. Conduct risk assessments B.
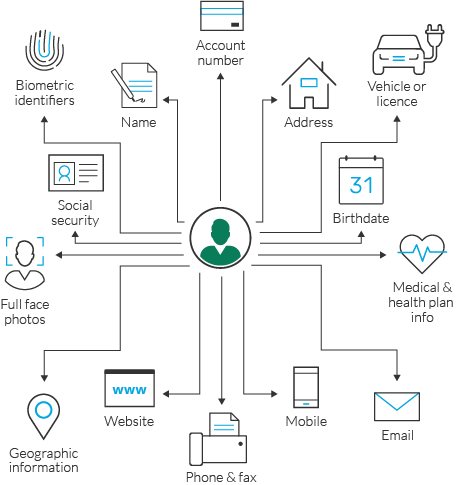
Examples of Personally Identifiable Information PII PII can include full name email address social security number phone number drivers license number IP address passport number home address geolocation and sensitive data like biometric data or medical records. Business mailing or email address. Personally Identifiable Information requires an analysis of PII in context.
In this context the information probably would not be considered sensitive. Why is PII so important. Full names first middle last name maiden name mothers maiden name alias.
Credentials for personal or business accounts Credentials for remote access software for business networks Access to data and phone services A list of passwords 16. However the classification of PII and non-PII is vague. Non-personally identifiable information non-PII is data that cannot be used on its own to trace or identify a personExamples of non-PII include but are not limited to.
However the same information in a database of patients at a clinic which treats. This data can not be used to distinguish or trace an individuals identity such as their name social security number date and place of birth bio-metric records etc. This document uses a broad definition of PII to identify as many potential sources of PII as possible eg databases shared network.
Organizations should identify all PII residing in their environment. Internet protocol IP media access control MAC Personal identification number. Which of the following is not an example of an administrative safeguard that organizations use to protect PII.
Social security number SSN passport number.

What Is Pii Learn How To Not Process Pii With Matomo

What Is Personally Identifiable Information Pii Data Security Imperva

/GettyImages-166419812-612e00ba43f6445498228e6638adfc3a.jpg)
Comments
Post a Comment